An open access journal
An open access journal
Exploring Machine Learning and Data Analysis Strategies for Telecom and Bank Card Fraud Patterns.
Abstract
Telecom fraud is a criminal activity that utilizes phones, the internet, and text messages to deceive victims into transferring funds. With the advancement of technology, telecom fraud methods continue to evolve, making the identification and prevention of these fraudulent activities increasingly important. This paper combines data provided by the organizing committee for data analysis and the establishment of a telecom and bank card fraud prediction model.
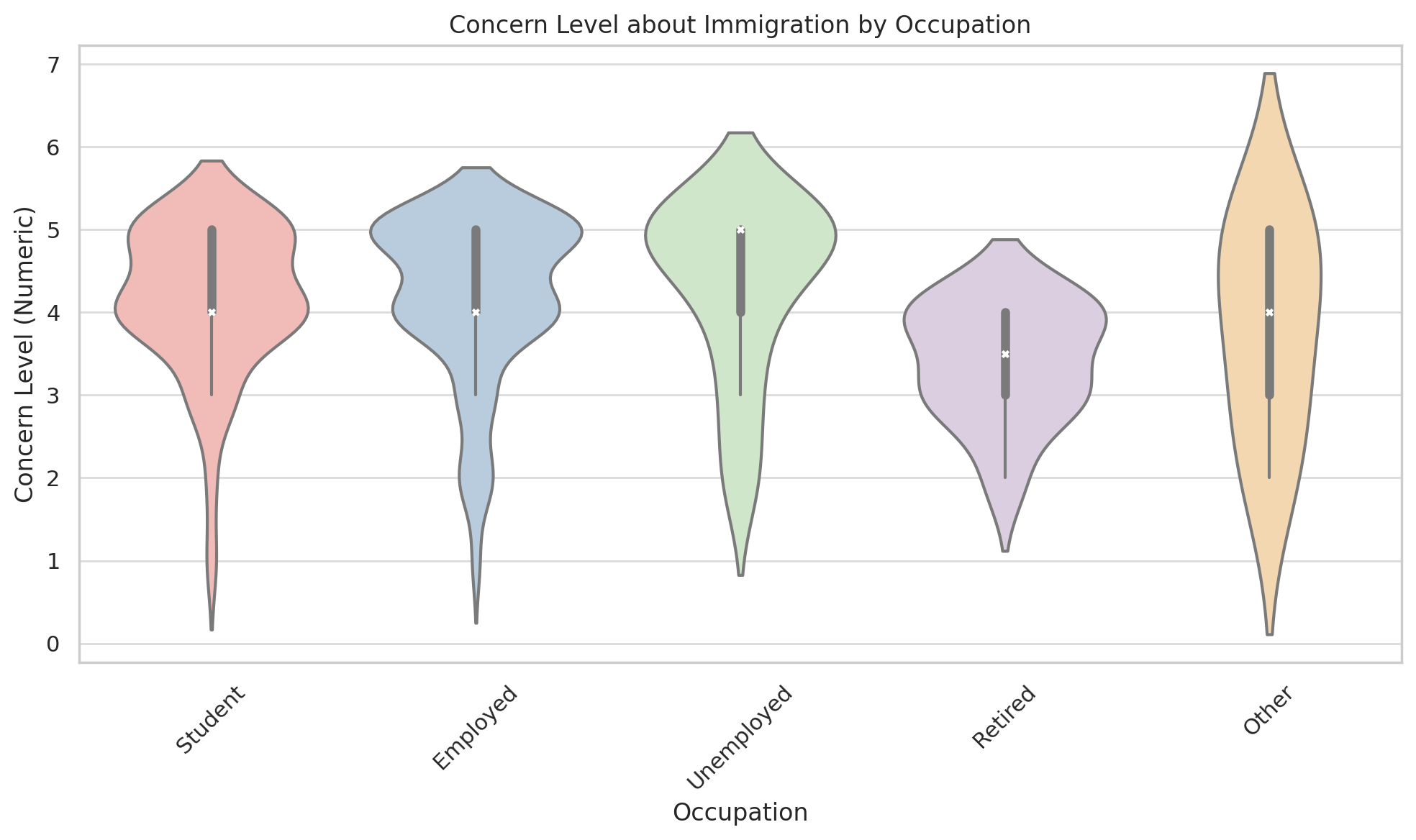
In Problem 1, data visualization techniques were used to analyze the environment in which telecom and bank card fraud occurs. Pie charts and bar charts were created to display the frequency of fraud occurrences and the ratio of online to offline fraud. The analysis revealed a higher incidence of telecom fraud in online environments, providing a basis for subsequent preventive strategies.
In Problem 2, we used a logistic regression model to analyze the impact of bank card usage (whether the card was used for transfers on a device and whether a PIN code was used for transactions) on the probability of telecom fraud. The results showed that using a PIN code significantly reduced the likelihood of fraud, suggesting that strengthening the use of PIN codes is an effective strategy in preventing telecom fraud.
In Problem 3, we tested the linearity and normality of variables, using Spearman’s correlation analysis and chi-square tests to reveal the correlation between factors such as the transaction amount ratio, whether transactions were conducted with the same bank, and whether transactions were made online. The in-depth analysis of these indicators aids in more accurately identifying potential fraudulent activities and provides feature importance for the prediction model.
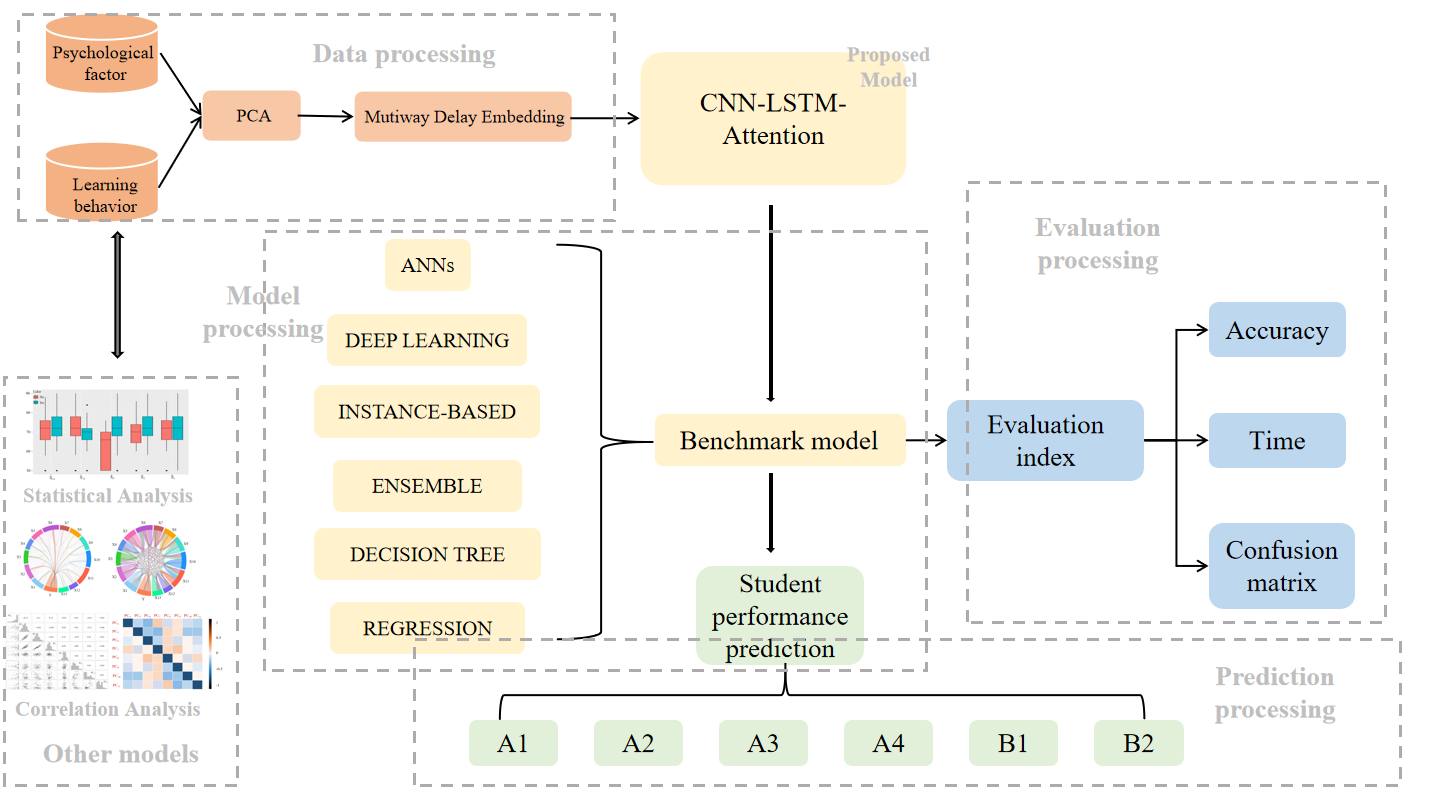
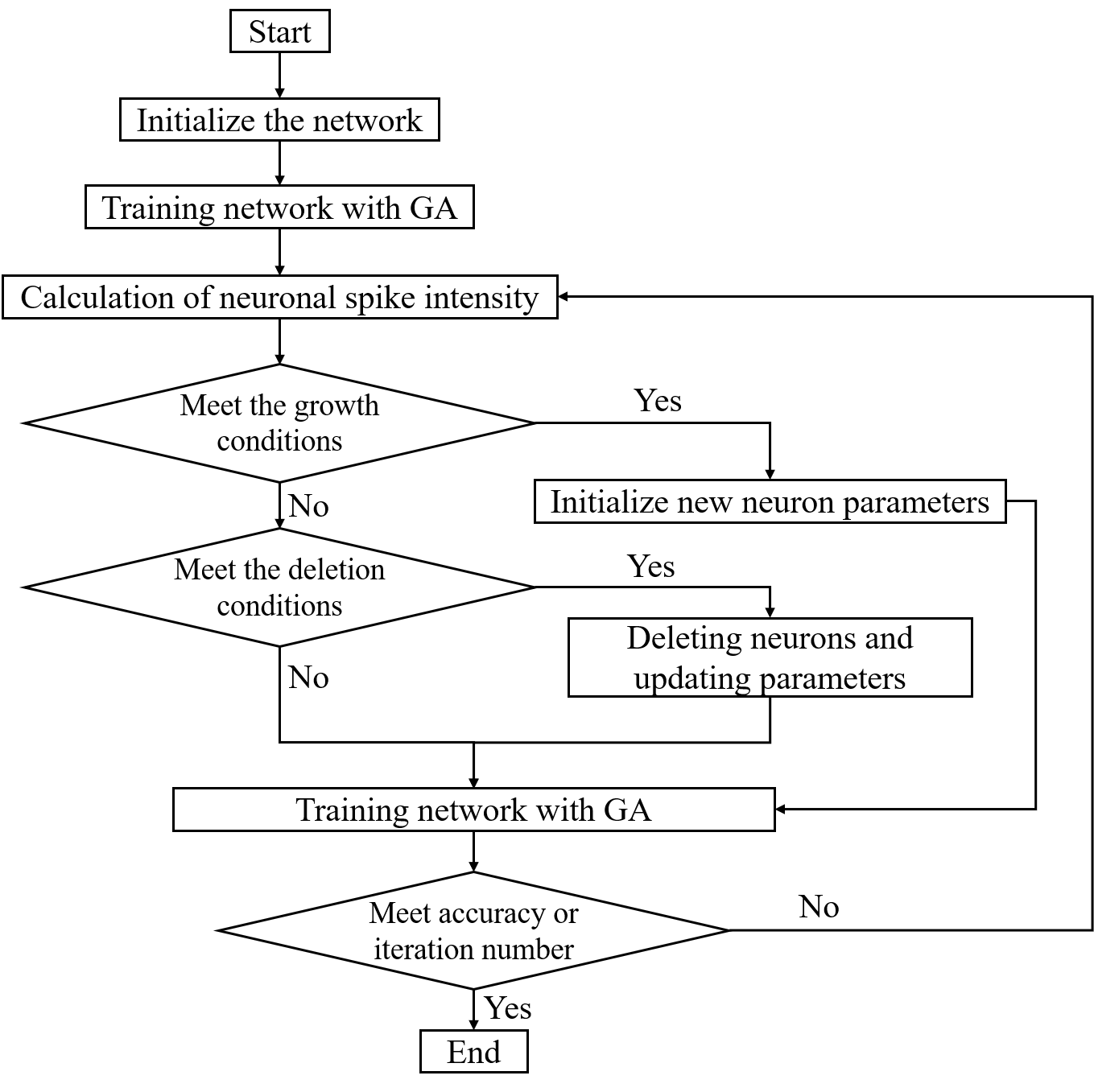
In Problem 4, convolutional neural network (CNN) models, long short-term memory (LSTM) models, and attention mechanisms were introduced. We employed stacking ensemble learning to integrate models, improved the attention mechanism, and added measures to prevent overfitting. Finally, we calculated accuracy, precision, recall, and F1 scores for each model. The results showed that the telecom and bank card fraud prediction model established in this paper achieved an accuracy of 99.99%, effectively predicting fraud. Based on the data analysis throughout this paper, we provide recommendations for public security departments, banks, and citizens to reduce the probability of telecom fraud.
In conclusion, this paper applies modern data analysis and machine learning techniques, with particular innovations in model integration and the application of attention mechanisms. Not only does this improve the prediction ability of the models, but it also validates their applicability and robustness through accuracy and error analysis. The research results are compared with existing technologies in a horizontal comparison and demonstrate the model's potential for future expansion, providing a promising outlook for telecom and bank card fraud detection.
Share and Cite
Article Metrics
References
- Chen Xiaolei, Xu Hui. Construction of the evidence system for telecom fraud cases [J]. Network Security Technology and Applications, 2024 (5): 139-141.
- Qin Yutian. The logical development and crime control of the core crime of fraud [J / OL]. Journal of Taiyuan University (Social Science Edition), 2024,25 (4): 95-104.
- Zhang Hao. Analysis on ecological Management of "black and grey Industry Chain" of telecom network fraud crime [J]. Network Security Technology and Applications, 2024 (4): 148-150.
- Xiao Song, Huang Jianwu. First-order approximated knife modified ridge type estimation in a binary logistic regression model [J]. Journal of Hunan University of Arts and Sciences (Natural Science Edition), 2024,36 (2): 6-13.
- Zhang Jian, Liu Lin, Li Qian. M-Score model optimization study based on nonlinear logistic regression [J]. Business Accounting, 2024 (10): 83-86.
- Liao Wen. Research and Application of User Loss prediction Model of Internet Finance Based on Data Mining [D / OL]. South China University of Technology, 2021.
- Zhao Zeming. Research on intelligent habitat mode and behavior prediction based on data mining technology [D / OL]. Harbin Institute of Technology, 2021.
- Li Hao, Zhao Qing, Cui Chenzhou, et al. A stellar spectral classification algorithm [J] based on the composite depth model of CNN and LSTM. Spectroscopy and spectral analysis, 2024,44 (6): 1668-1675.
- Zhao Zeming. Research on intelligent habitat mode and behavior prediction based on data mining technology [D]. Harbin Institute of Technology, 2021.
- Li Huifeng, Li Tiecheng, Li Weixun. Application of Fuzzy Theory in Communication Network Evaluation of Smart Substation [J]. Mechanical Design and Manufacture, 2024 (04): 28-32 + 37.
- Cheng Junhan, Wang Shuli, CAI Zhiyuan. Residual service life prediction of lithium battery based on AE-LSTM [J]. Electrical Appliances and Energy Efficiency Management Technology, 2023 (09): 69-75.
- Liu Shengjiu, Liang Shupeng, Liu Ying, et al. Analysis and application of hypergraph entropy [C] / / Chinese Society of Automation. Proceedings of the 2023 China Automation Conference. [Publisher unknown], 2023:6.
- Zhang Haiyang, Chen Yuming, Zeng Nianfeng, et al. Credit card fraud detection based on the XGBoost and LR fusion model [J]. Journal of Chongqing University of Technology (Natural Science), 2024,38 (03): 195-200.